WAN security
As broadcasters deploy networking throughout their facilities, security is a constant concern.
Many facilities have developed comprehensive security policies and installed technology to protect their facilities from attacks. In many cases, the security policy includes the proviso that the broadcast LAN is sacrosanct. This means network designers and engineers have not permitted any connection between the broadcast LAN and any other network in the facility.
Transfer of program logs, as-run logs and other data between the on-air network and other systems occurs via removable media such as floppy disk or USB drive. The interface is typically through a dedicated computer that is meticulously maintained with the latest antivirus scanning software. Content is not allowed to enter the LAN from any other source, and connection of laptops and other unauthorized computers to the broadcast LAN is prohibited.
But times are changing, and security policies will inevitably have to change as well. Gone are the days when master control sat in isolation, only accepting videotapes and printed logs, returning marked-up copies of the logs to traffic at the end of the day.
We may have secretly enjoyed the sight of a dejected commercial salesperson being banished from master control after showing up with a spot 15 minutes before airtime. However, now it is our responsibility to deploy the best technology and to develop the best policies to get every piece of programming and commercial on the air — even if that content arrives at the last minute. Furthermore, as station consolidation proceeds apace, management demands more visibility and control over what is happening in on-air facilities.
When you put all of this together, the inevitable conclusion is that the broadcast LAN will be connected to other LANs in the facility. Not only that, for many broadcasters, it means the broadcast LAN will need to be tied to the outside world as well. This is not an altogether comforting thought to those whose continued employment is tied directly to the ability to keep a signal on the air.
WAN vs. the Internet
The professional video industry's #1 source for news, trends and product and tech information. Sign up below.
The prospect of connecting the broadcast LAN to other networks inside a facility causes engineers concern. The idea of connecting that LAN to the Internet may cause even more concern, and with good reason. The Internet is downright terrifying.
I maintain several servers on the Internet, and on an average day, I get about 2000 break-in attempts. This is probably not comforting news to someone who has just been told that the company is establishing a WAN so they can hook all remote automation systems to a central traffic system.
As Figure 1 shows, a LAN is a local area network, and a WAN is a wide area network. A LAN exists within your facility, while a WAN extends beyond your facility. Simply put, network equipment at the edge of a LAN communicates with network equipment at a remote facility to tie these facilities together.
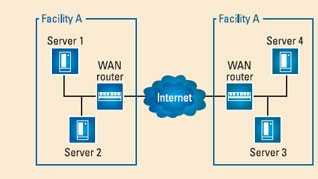
WANs have many uses in broadcasting. For example, a WAN might allow a centralized traffic system to distribute logs to several remote automation systems, or it might be used to deliver audio voice-overs from a production facility to any number of network affiliates. WAN traffic travels over a link layer network, whether that is Ethernet, frame relay or another packetized transport mechanism.
A secure but expensive way to interconnect LANs is with a WAN using dedicated leased lines. To do this, a company purchases dedicated lines for use between its facilities. No outside traffic is permitted. If access to the WAN is controlled, this results in a secure way to connect mission-critical equipment.
Of course, most service providers charge more for dedicated leased lines because they cannot run other traffic over them. Unfortunately, because they are expensive, few broadcasters use dedicated leased lines anymore. The Internet is much less expensive.
Security techniques
So what is the alternative? Many corporations transfer private data over WANs every day. How do they do it? Why would a bank or other financial organization be comfortable transmitting highly personal information over the Internet, especially when they know that crooks are deliberately trying to gain access to this information?
The answer is that they use proven security techniques, they actively audit their security systems, they employ active detection to proactively determine if a break-in has occurred, and in some cases, they hire security firms to attempt to hack into their systems. Broadcasters can use a similar approach when developing WANs that transport data over the Internet.
The following are things you can do to secure your facility.
- EncryptionUse strong encryption on all WAN traffic. What constitutes strong encryption changes over time, so you should talk with your equipment vendors and potentially talk to an independent security consultant when deciding what encryption to use.
- AuthenticationUse strong authentication mechanisms, not only on your WAN, but on servers on your LAN as well. Most security consultants recommend abandoning the old username/password authentication mechanism. It has been proven over and over that this system is easy to crack.Many organizations use two-factor authentication. Usually two-factor authentication consists of something you have and something you know. An example of this is the badge system at all federally controlled airports. The badge is something the employees have, and the code they enter after they swipe the card is something they know.In the computer world, you may have a private key (a long randomly generated sequence) stored on your computer (something you have). This is used along with a passphrase (something you know) to verify that you are who you say you are.
- AuditConduct an audit of your security policy and security systems. Think about the security policy and whether it makes sense. Put yourself in the position of someone who wants to gain access to your network or disrupt it. No one knows your processes better than you do. Before you talk to an outside consultant, think through the security policies yourself.
- MonitorConsider installing systems that monitor your network for suspicious activity. When these systems see something out of the ordinary, they send out notifications by e-mail, SMS or telephone. In some cases, these systems can take steps to shut down the WAN or other link without human intervention.One word of caution: Be sure you know the total cost of using these systems. It takes an expert to configure and maintain them.
- Update operating systemsRun the latest versions of operating systems in all servers and network edge devices. Have a system automatically notify you when updates are available. Check for upgrades before you perform an initial installation. Do not assume that just because a device arrived from the manufacturer that it has the latest software upgrades.
- Hire a security expertHire a security expert to analyze your network and to make recommendations. When you hire someone from outside your organization, do not turn everything over to him. You will get much better results if you engage in a partnership with your consultants.
Conclusion
A WAN linked with the Internet can be a cost-effective and secure solution to the dilemma many broadcasters face in connecting critical systems that are geographically separated.
Brad Gilmer is executive director of the Advanced Media Workflow Association, executive director of the Video Services Forum and president of Gilmer & Associates.
Send questions and comments to:brad.gilmer@penton.com
