Priming the Pump for Secure Storage
How ISO/IEC standards can support storage security data and practices

Security guidance for ecosystems associated with data and storage systems had for many years focused principally on the protection of their associated systems, such as hardware, connections and processes used in backup or duplication. Other guiding objectives stayed fixed on the general support of evolving information security standards, per ISO/IEC 27000 directives and a collection of closely bound and integrated documents.
Standards have played important and strong roles in molding information technologies to become a harmonized set of criteria that has guided hardware, software and implementation. As a part of the entire ISO/IEC 27000 family of standards, a specific suite of documents is published by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) under the joint technical committees (JTC) in ISO/IEC JTC 1/SC 27 for IT Security techniques. The ISO/IEC established a series of continually developing documents, which grew out of industry’s rapid growth in IT, storage and networking.
The JTC was founded in 1990 when an earlier subcommittee (JTC 1/SC 20) moved outside of the field of security techniques associated with phrases such as: “secret-key techniques,” “public-key techniques” and “data encryption protocols.” These late 1990s techniques were later disbanded in favor of emerging techniques driven by new products, advanced needs and obsolete applications.
As is often the process in standards development, these root-1990 subcommittees, and beyond into modern day, have systematically altered various groups’ scopes and associated working groups’ efforts to meet current (at that particular time) demands for standardization. As such, numerous details, trials and tribulations often appear in more up-to-date applications as the technologies mature, emerge or obsolesce.
Data, in the form of assets, is of paramount importance to individuals, industry and enterprise. Many understand some of the founding principles (backup, for example); yet others have no foundational practice or reasoning as to why one approach is taken compared to another. This issue opens the topic of storage security as applied to using some of the ISO/IEC standards to support the safe keeping of media-related data and its practices.
CORE DATA PROTECTION
Like most network or storage system administrators, there are three core issues associated with data protection: privacy, information security and assurance, plus the storage (data) itself (Fig. 1). The goals are associated with protection centered on the notion that “all security goals and objectives be continuously maintained irrespective of any system complexity, variation in performance or the granularity of individual fidelity”—that is, without compromise.
Assuring all these goals are maintained is paramount to elevating the sustainability of the system, the integrity of the storage (i.e., its data) and the appropriate level of privacy, protection and information at all levels. When one realizes the broad areas such approaches might need to address, the details could be daunting. And this is precisely why the ISO/IEC groups assembled a series of documented guidelines and processes by which to follow.
The professional video industry's #1 source for news, trends and product and tech information. Sign up below.
However, the approaches can be confusing depending upon which versions or at what time your planning was first introduced. For example, in storage security guideline ISO/IEC 27040, the concept of “data protection” is not specifically addressed, despite a high degree of insight, which is presented in the document. Instead, this standard aims to establish security controls, which in turn helps elevate awareness of storage security through additional feature sets and best practices.
DATA PROTECTION CONTROLS
Since the starting point, file-based data workflows for media, audio/video and motion picture production depended upon and utilized simple storage management solutions with a modest degree of structure for its direct data protection. Early in that progression, users leveraged external storage solutions (e.g., removable drives) as a fundamental backup solution. Network storage was a “few and far between” alternative. These methods were sufficient, initially, but changed dramatically as storage volumes accelerated exponentially.
Likewise, only a modest number of users (and systems) had any serious concern for data protection—primarily because self-management and isolation was an easy, relatively straightforward process unencumbered by hackers, pirates and disruptors at that time. Hardware integrity posed more problems than content stealing prevention, due in part to proprietary codecs and self-regulated, insulated code support channels
Today, of course, we have an entirely different perspective. Exponential volumes of data have driven business continuity and disaster recovery requirements upward. Backup copies are now built to protect against data loss, one of a continually expanding set of data protection controls. Implementation guidance outlined in the ISO/IEC 27000 series (Table 1), prescribes organization requirements for information backup, including, but not limited to, software, systems and management policies.
Essential information beyond simply the data must be retained in facilities that can be run with the appropriate hardware and software tool sets to recover duplicate data sets should the original hardware be compromised. Recovery processes should be documented, itemized and their implementation procedures routinely tested should the main facilities be lost or destroyed.
Operational processes, such as how to monitor backup execution, must be reviewed against new software application versions whether locally hosted or in the cloud.
SECURING BACKUPS
At first the concept for securing backups, documented in 2013 under ISO/IEC 27002, may seem a bit archaic in the 2020 era of cloud-based protection, but they should not be forgotten or discarded by any means. In fact, the requirements for storage security, related to (secure) backups, are now clearly ingrained in the ISO/IEC documents.
Backup security is just one of the pillars for overall security on a broad scale. Today, it makes further sense to have a functioning system “in the cloud,” yet it does no good if the procedures are not consistent. Cloud vs. datacenter practices should often both be reviewed; have their routines updated and harmonized; and assure that all the code “tricks” created by developers remain in line with each other.
Extensions to storage security practices, which may now be ported to a cloud environment, could also be replicated in another “offsite” datacenter. Cloud may be for deep archive, with the data center being for rapid recovery—the choice is up to the business owner and administration.
TRUST AND VERIFY
Updated extensions include guidelines from a 2016 update of ISO/IEC 27004, which outlines “the effectiveness of measuring information security.” The 2016 update completely restructured the previous (original) document expanding it with a new purpose and putting it into current rules per the ISO/IEC Directives-Part 2.
Specific changes identified in the updates now lean toward media encryption, and operator authentication and authorization. They harmonize security practices with specifics identified for both backup systems and storage media. The concept of the “trusted” individual, component and/or system is now added, with the inclusion of a cleared and vetted or bonded individual.
Audit trail identification for backup processes and a clear path to verify the backup was actually performed are now required. Furthermore, a means to physically prove that restoration requirements are being met is necessary for proper certification. In effect, the backup is now trusted and the processes are now verified, per the standards.
FINER POINTS
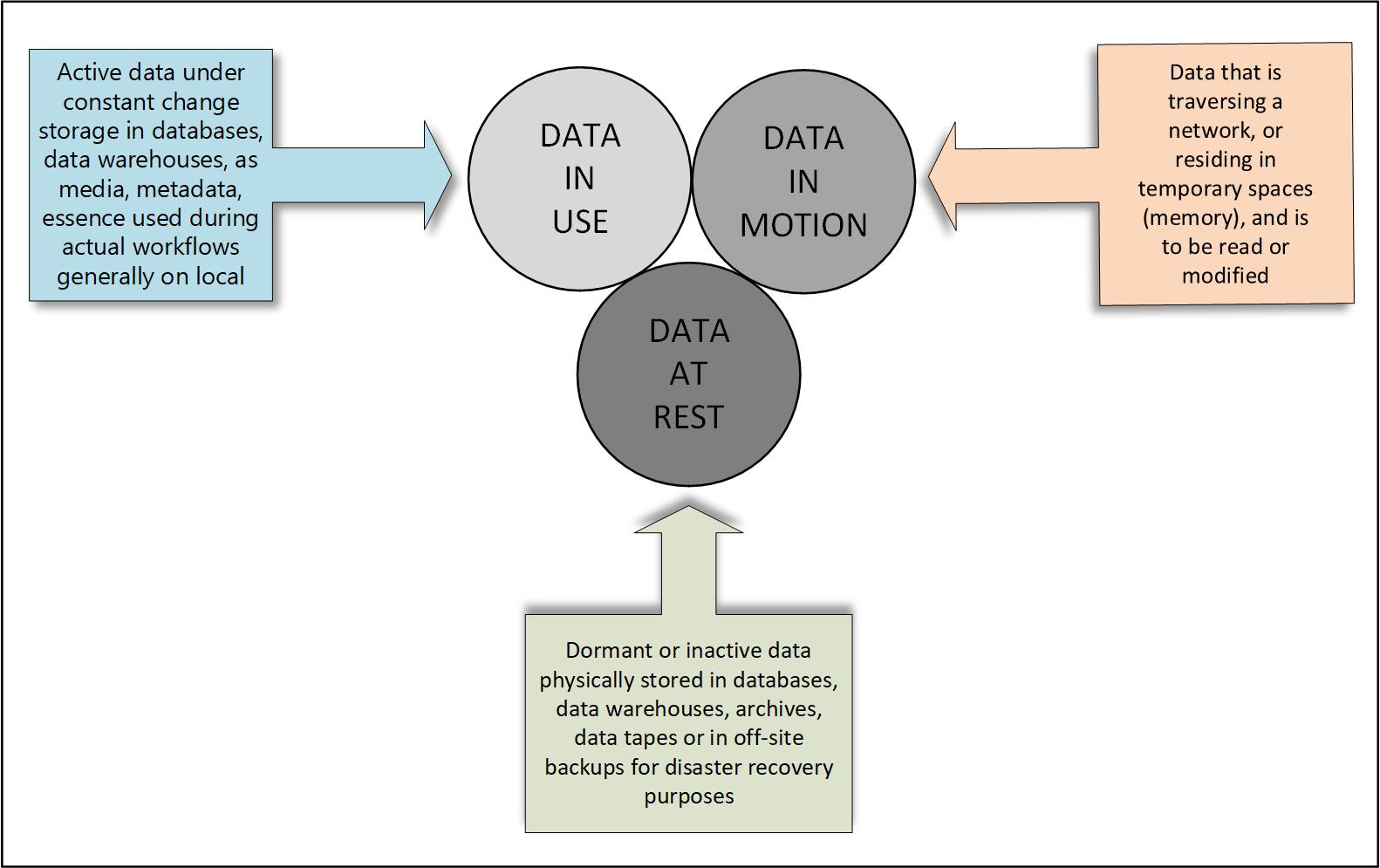
ISO/IEC standards go much deeper and can be studied if you have access to or subscribe to the specific documents—most of which are not free. In part, data availability recommendations will include procedures for reliability, fault-tolerance and the requirements for performance of the data itself. Users must insure (and assure) against unauthorized access using technologies such as “data in motion” encryption, i.e., data that is in transit or in flight, is encrypted when the data is in the process of being moved (transported) between locations in either the facility, the computer and/or the network (Fig. 2).
Like the practices and procedures found in well-known industrial efforts, such as in ISO 9000-certified facilities, should have similar concepts and approaches to those well entrenched in IT and storage solutions. Each of the ISO/IEC-subcommittee’s agendas helps to support the practices and provide sustainability across the industry with consistency. Appropriate follow through by all the storage disciplines should be expected.
BLOCKCHAIN CHANGES THE COMPLEXION
Finally, we hear a lot of new uses and applications of blockchain, which is making data more secure, again. Transactional interchange of data that is untraceable, inaccessible and only known by the sender and the designated receiver—irrespective of the number of parties—is changing how content, contracts and transactions are being handled. The interchange of that data is so private and so secure that it is highly likely it will change the rules of storage and security forever. Stay tuned for upcoming topics on blockchain and how it will make the world a safer place for technologies.
Karl Paulsen is a SMPTE Fellow and frequent contributor to TV Technology, focusing on emerging technologies and workflows for the industry. Contact Karl at ivideoserver@gmail.com.

Karl Paulsen recently retired as a CTO and has regularly contributed to TV Tech on topics related to media, networking, workflow, cloud and systemization for the media and entertainment industry. He is a SMPTE Fellow with more than 50 years of engineering and managerial experience in commercial TV and radio broadcasting. For over 25 years he has written on featured topics in TV Tech magazine—penning the magazine’s “Storage and Media Technologies” and “Cloudspotter’s Journal” columns.