The Challenges of Cloud Computing in 2025
Data security and protection methods to consider in the coming year

Cloud computing administrators and their superiors probably have been asked at least once in their life, “What keeps you up at night?” An AI-overview answer (courtesy Google AI) came back with this answer: “Essentially, the responsibility of ensuring critical data and applications remain accessible and secure within a dynamic cloud environment.” But this “overview” didn’t really answer the question, so this article may help open your eyes to what’s coming.
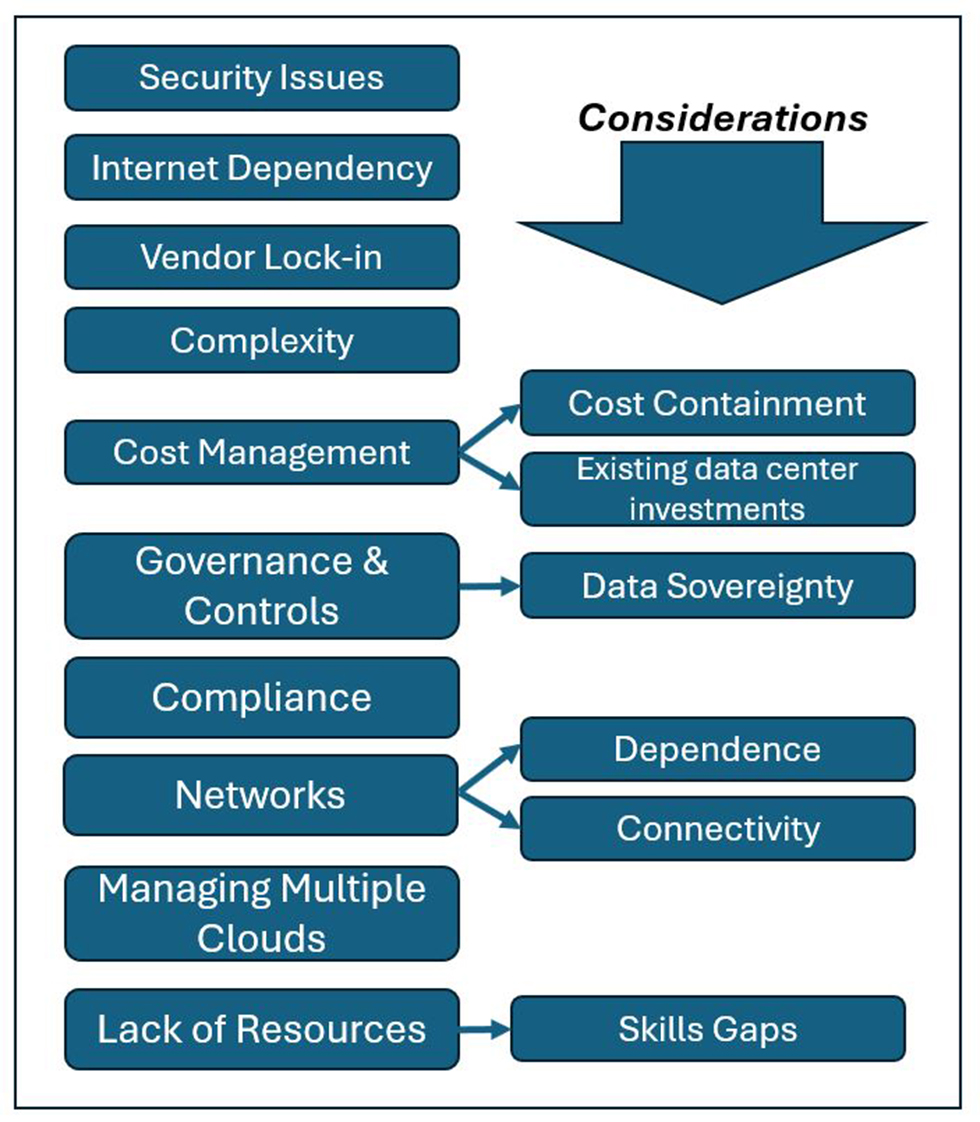
Fig. 1 summarizes the major points discovered in the research for this article and, not surprisingly, most of the findings from several sources round out to about the same bullet points from 2024 and before. We’ll take some of these points and practices apart in the following segments and see if you agree on the importance of their implementation.
The Security Elephant
The elephant in the room is most likely security. Like many other branches of technology, security is a pressing concern in cloud-based computing—no surprise here, and certainly not contained to just cloud. In general, security has become the biggest issue for all organizations—irrespective of size, revenues or locations (ground, cloud or home).
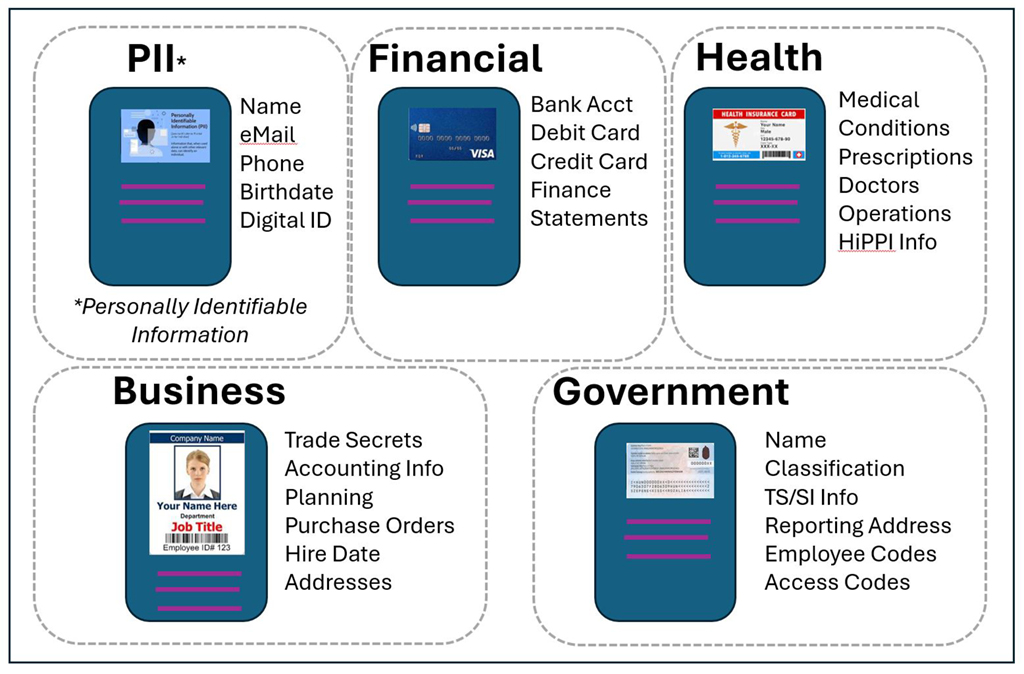
Refining the security topic a bit brings into play “sensitive” data, which is another major concern. Sensitive data is defined as information that, if disclosed, misused or accessed without authorization, could result in harm, discrimination or adverse consequences for the individual to whom the data pertains (per a simple Google search).
Fig. 2 briefly summarizes the categories of sensitive data for any organization. However, if your organization associates at a government (e.g., intelligence community) level, your people may require a top-secret (TS) clearance, the most restrictive level. TS-data is that information which can cause grave damage to national security if disclosed without authorization.
In this example, performance of your systems (ground or cloud) must meet TS-level criteria, and your administrative people must be reinvestigated for continued eligibility every five years.
Complex Challenges
Security risks for cloud replicate those found in everyday activities with mobile devices, home computing, work compute environments and daily life. Included in the risk-list and prevention methodologies are avoiding phishing emails, forged messages (e.g., fictitious representations) and ensuring strict user access control policies are in place.
The professional video industry's #1 source for news, trends and product and tech information. Sign up below.
Securing data (including its accessibility) is becoming increasingly complex and challenging. Those organizations with poor data management practices, weak network security, little, poor or no encryption methods, and/or a lack of endpoint protection may face significant challenges in 2025 and beyond.
Primary Methods of Protection
Data is one of the most valuable assets to the organization or individual. Learning basic, primary methods for protecting sensitive or confidential data is critical to the organization to avoid potential data breaches or data loss. Data loss can be devastating, often resulting in identity theft, loss of business or exposure of classified or confidential information.
Data classification is a good first step in managing your organization’s information—whether in the cloud or on the ground. Data classification are those processes whereby the user organizes its data into multiple categories within a system to make it easier to access and secure.
Ranking the data by sensitivity to reduce storage and backup costs is just one step. Such policies can greatly reduce inefficiencies and create better safeguards whether for personal or company data. This further helps assess how sensitive data is used, which permissions or accessibility can be administered, all of which increase data privacy and security for third and fourth parties.
Data Protection Impact Assessments
Any time data storage or data processing is involved, it’s important to assess and identify each potential risk before they occur. Data protection impact assessments (DPIA) are active (live) tools designed to help organizations secure their data if they involve significant risk to exposure of personal information.
For the United States, this makes cloud data management more complex if your organization deals with any international (i.e., EU) people or companies. DPIA defines data processing roles within the company, data flow between systems and individuals, and the security policy in the event of a cyberattack.
Encryption and Masking
Organizations operating with highly sensitive data (in the cloud or on the ground) should consider encryption to prevent unauthorized parties from accessing it. Using complex algorithms and ciphers, data can then be protected from being stolen or exposed during a cyber-event. Blockchain is a methodology used to protect authenticity and identification of data alteration. It is often used to protect sensitive media (motion pictures, especially those in production) and in the exchange or execution of contracts.
U.S. military and government entities have used data encryption to transmit and receive any classified communications for decades. For businesses, some cloud service providers may also provide those capabilities for additional fees.
Data masking, similar in practice to data encryption, replaces the original data with fictional data to protect its security. Masking processes are generally for internal use to prevent developers, testers or researchers from accessing sensitive data—thus mitigating potential leaks or breaches by disgruntled employees or human errors (the biggest cause of security violations).
Data masking is sometimes used in the testing process to evaluate patching services/systems, various security protocols, or to involve building new features without using real user data.
Password Protection and Authentication
Most of us are, by now, aware of two-factor authentication (2FA) or multifactor authentication (MFA), which is used by banks, credit card companies and such to protect user accounts and mitigate enterprise breaches.
2FAs or MFAs are the easiest—and most protective of the ata security practices—and while a bit more complicated in a cloud environment, are not beyond implementation with a couple extra steps to access the cloud or the network.
According to ZDNet, Microsoft revealed 99.9% of compromised accounts did not use MFA, and that only 11% of enterprise accounts had MFA in place.
Strong Network Security
This is not a single-solution-only practice. Protecting the network often employs many different security solutions to best protect data from being compromised (i.e., stolen or simply accessed). IT managers must create and manage a secure environment on-prem before leveraging the advantages of the cloud for additional services.
Since the cloud essentially “sits at the edge” of the network, administrators must feel confident that the cloud side of the enterprise meets a minimum set of criteria to facilitate the needs of the organization.
Solutions include antivirus and antimalware software applications, data loss protection (DLP) practices, intrusion detection systems (IDS) and prevention (IPS), proper firewalls, VPNs and endpoint response and detection (EDR). Additional suggestions include network segmentation and secure data removal tools.
Additional Concerns in 2025 for Cloud
Briefly, in addition to a well-defined and properly managed security solution set, the other suggestions to consider when looking into the cloud for enterprise operations include:
- Internet dependency: Given that cloud computing generally relies on internet connectivity, should there be an outage, businesses might not be able to access their data or applications. Providing a hardened alternative (dedicated lines) to/from the access points can be valuable, but costly, too.
- Vendor lock-in: Businesses using cloud computing are ill-advised to become dependent on a specific single vendor, making it difficult to switch providers should something unforeseen occur.
- Complexity: For businesses that are new to the technology, cloud computing can be complex. Be prepared for a lengthy startup period and engage a solutions architect who is experienced in what you do and with various cloud provider solutions.
- Cost management: Spending can be a significant challenge. Be certain your financial officers are prepared for the sometimes rapidly changing cost structures and “bring them along” in the process.
- Skills: The skills gap is one of the biggest challenges for cloud computing technologies. These individuals are hard to find, sometimes hard to engage and can cost a pretty penny to employ.
This is by no means a “complete” list of the 2025 and beyond” cloud-computing concerns, but they hit the high points of the topics. If you’re even slightly concerned about how to address these issues, hire a professional to get you through the planning and implementation. You’ll be glad you did.

Karl Paulsen recently retired as a CTO and has regularly contributed to TV Tech on topics related to media, networking, workflow, cloud and systemization for the media and entertainment industry. He is a SMPTE Fellow with more than 50 years of engineering and managerial experience in commercial TV and radio broadcasting. For over 25 years he has written on featured topics in TV Tech magazine—penning the magazine’s “Storage and Media Technologies” and “Cloudspotter’s Journal” columns.