Best Practices for ST 2110 Cybersecurity
COLLEGE STATION, TEXAS—The television broadcast technical plant is changing or has changed for many. The traditional baseband based serial digital interface (SDI) commonplace since the inception of digital television is being replaced by an IP-based infrastructure. The migration to an all-IP infrastructure brings several advantages, including:
- Cost savings by using commercial, off-the-shelf (COTS) IT hardware. Enterprise routers and switches have enormous economies of scale compared to the broadcast world’s purpose-built, industry-specific infrastructure.
- Greater system workflow flexibility. The inherent architecture flexibility provides for a change in workflow processes without a system re-wire commonly found in the baseband SDI plant. With a COTS Ethernet switch, high-capacity, non-blocking signal routing can be implemented in far less space than the traditional matrix SDI router.
- Format and resolution agnostic. Enterprises and streaming video service providers already use COTS infrastructure for a wide variety of formats and resolutions, from 720p through 1080p at 60fps and 4k. The use of IT industry standards also enables the high levels of interoperability commonly found among COTS equipment manufacturers.
- Simplified interconnection wiring. Installation costs are significantly reduced because less interconnection cabling means less labor. The SDI plant’s fixed signal path is replaced with a “star” architecture found in enterprise IT networks. System changes also are implemented by software configuration rather than facility re-cabling.
The use of an IP network in a broadcast facility has been commonplace for some time now. One example is the familiar RJ-45 Ethernet jack on many broadcast devices. Use of the IP network has been primarily for command and control, monitoring or file transfer.
But when an IP network is mentioned in the context of transporting real-time broadcast media, an instant lack of trust is often a common response. Many broadcast professionals are simply unable to accept the perceived risk involved for mission-critical content transmission. The “belt and suspenders” mindset of the broadcast engineer simply does not permit the perceived unreliable operation found in the IP environment. Reinforcement for this mindset is often obtained from one’s personal experience with the Internet.
ENABLING PROFESSIONAL MEDIA OVER MANAGED IP NETWORKS
To enable interoperability between system components from different manufacturers, the Society of Motion Picture and Television Engineers (SMPTE) established the ST 2110 standard. SMPTE 2110 is considered an umbrella standard, or a family of individual functional standards, that allow for the transmission of uncompressed audio and video over an IP network.
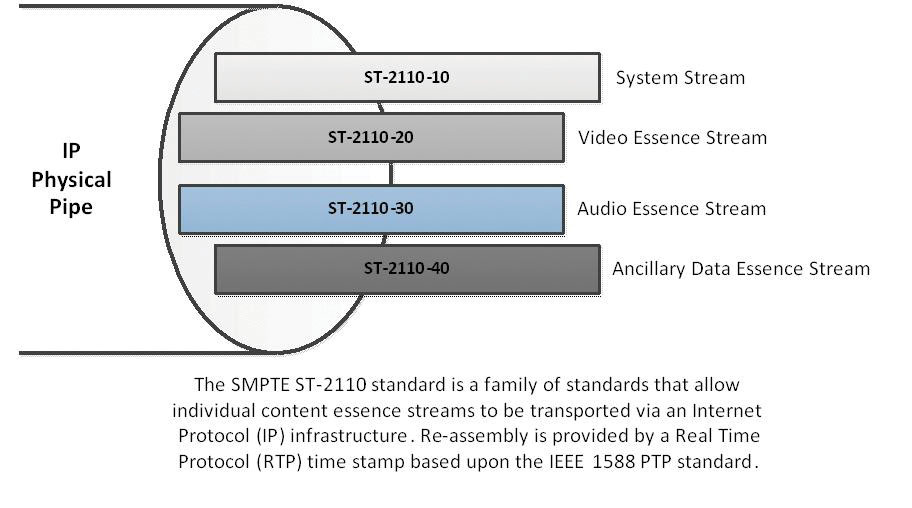
SMPTE 2110 is a suite of standards for transmission of “professional media over managed IP networks.” Audio, video and ancillary data are treated as separate, uncompressed essence data streams. Individual standards focus upon functional components of the suite, such as video (ST 2110-20) or audio (ST 2110-30). Ancillary data may include captioning data (ST 2110-40) that is associated with the media essence streams. A unique feature of ST 2110 allows essence data streams to be sent or routed over different physical paths and re-assembled at a destination end point by the incorporation of a synchronization mechanism (ST 2110-10).
Several SMPTE standards incorporate established Internet Engineering Task Force (IETF) Request for Comments (RFC) provisions into the standards. Examples include the ST 2110-20 standard incorporating the IETC RFC #4175 for uncompressed video transmission and the ST 2110-10 system standard incorporating the IETF RFC #3550 Real Time Protocol (RTP). The IETF RFC’s are considered the “Bible” of IP networking.
It is important to make a couple of critical distinctions regarding the SMPTE ST 2110 standard. First, what is known as the public “Internet” is not the intended physical transport platform. By definition stated in the ST 2110 title, a “managed” IP network is the transport platform. A managed IP network is a private network that is built on private physical facilities or more likely a telco common carrier provided Multiprotocol Label Switching (MPLS) network. Performance can be specified in a Service Level Agreement (SLA) to ensure reliable delivery of real-media content such as high-definition, uncompressed video. Differentiated services are utilized to meet and maintain a contracted Quality of Service (QoS).
In contrast, the public Internet is a maze of independent interconnected networks with no end-to-end performance coordination or governance. Thus, the term “best effort” is used to describe the QoS of the public Internet. This is simply not an appropriate network choice in which to implement SMPTE ST 2110.
THE CIA TRIAD OF CYBERSECURITY
The private nature of the physical network platform also becomes a first step in mitigating cybersecurity vulnerabilities. Nevertheless, ST 2110 is an IP-based data network, so the IT industry’s accepted security practices should be deployed in any implementation.
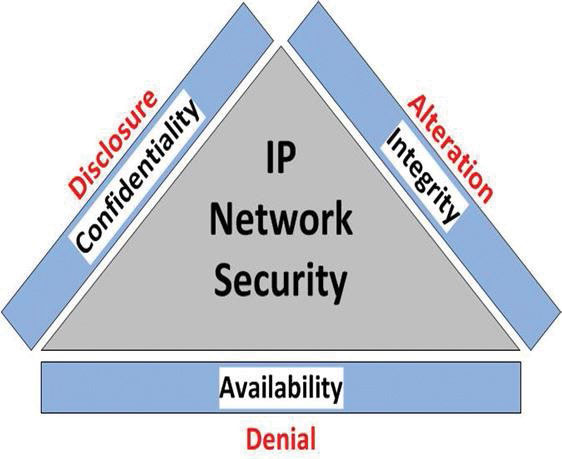
Network cybersecurity mitigation involves a number of individual steps or practices rather than one single step. Overall, the goal of network security is to meet the attributes defined by the “CIA Triad” as illustrated by Fig. 2. The triad is based upon the three attributes of: Confidentiality, Integrity and Availability. It should be noted that the phrase “AIC Triad” may also be used to avoid confusion with a US government agency of the same acronym.
Confidentiality refers to the ability of the network infrastructure to not allow disclosure of the data or information traversing the network infrastructure to any unauthorized user or host. Integrity refers to the ability of the network to ensure that the data has not been altered by an unauthorized user or host. And availability refers to the ability of the network infrastructure to ensure that resources are available only to authorized users or hosts.
[Read: Need To Know: Cybersecurity]
Cybersecurity events such as a Denial of Service (DoS) attack or a Distributed Denial of Service (DDoS) attack target the availability attribute by impacting access to the network resources by legitimate users. A Man in the Middle (MITM) attack seeks to destroy the integrity attribute by altering the data or information traversing the network.
Industry best practices begin with network design as the first step in cyber-security threat mitigation. The network is segmented or layered into functional areas as dictated by the business case use, regulatory policy or organizational policy. Each layer or segment has unique use or purpose with an established security access policy. Inner layers are considered the core network segments and are the most secure.
The characteristics of an MPLS network provide an economical platform for ST 2110 implementation.
Other security attributes involve physical network infrastructure equipment protection from tampering through locked enclosures, cabinets or cages. Implementation of Ethernet switch port security is another capability that a managed switch offers to control what host device can be attached to a switch port. Packet filtering can be implemented by an Access Control List (ACL) to allow select host interoperability between network segments. The ACL filtering can be based upon several IP header fields such as addresses, protocol and port number.
Infrastructure equipment management should be implemented in an out-of-band manner. Out-of-band management also allows the use of the public Internet for accessibility implemented in a secure manner such as an encrypted Virtual Private Network (VPN) connection to the management network. This approach provides an air-gap between content transport network segments and the management network.
All of these outlined practices come together to define a secure network rather than complying with a single attribute. Cybersecurity can’t be ignored or left as an afterthought. At the end of the day, the broadcast engineer should have trust and confidence in a SMPTE ST 2110 network that is implemented as intended by the published standard utilizing established industry security practices.
Wayne M. Pecena is a IEEE BTS Distinguished Lecturer and Director of Engineering, Texas A&M University, KAMU FM & TV.
Get the TV Tech Newsletter
The professional video industry's #1 source for news, trends and product and tech information. Sign up below.
