Cybersecurity and Accessible Storage Trends
EIGHTY FOUR, PA.—We now live in a world where organizations are more aware of cyberthreats than ever before. Cybercrime has now surpassed the profitability of illegal drug trafficking. Many organizations that interchange information are looking at myriad defensive measures to help keep business, industry and personal data secure. This elevated focus now includes storage systems as well as networks and other computer resources.
“There is no such thing as perfect security,” said cybersecurity firm FireEye in its annual Mandiant Threat Report issued in mid-2015. Threat actors have evolved to encompass a larger scope of targets and are using a broader skillset to achieve their goals. Determined threat actors are always finding a way through a gap in security; thus bringing the media and entertainment industry into sharper focus.
VULNERABILITY TO ATTACKS
As storage systems have become more entangled in network-based communications, they have become equally vulnerable to similar kinds of threats and attacks. System designers and network administrators who focus on managing storage must now consider advanced approaches to security aimed at protecting their most valued resource— their digital files as media assets.
Open standards are helping to drive storage vendors’ participation and interaction in finding effective methods for asset protection. Processes and procedures regularly being developed by a broad range of formal standards development organizations include industry forums and associations such as the Storage Network Industry Association and the Distributed Management Task Force. Teams working across all disciplines of storage and networking continue to provide a strong leadership role in establishing security criteria.
Standards organizations promote IT security objectives through parent committees (e.g., ISO/IEC JTC1 SC27) where security topics are addressed by active working groups that interact with industry to find acceptable and deployable preventative measures for security. Some of the groups address cryptography and security mechanisms (as SC27 WG2); security controls and services (as SC27 WG4); and the management of information and security systems for IT security evaluation and assurance.
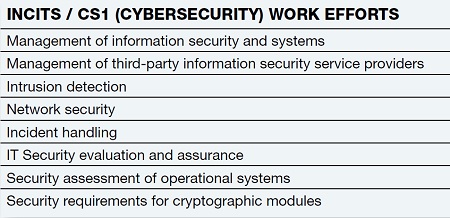
Table 1: Cybersecurity work efforts of the INCITS (T10) and CS1 groups who provide direction and standards for industrySECURITY FOR STORAGE
Storage security standards groups, such as for Small Computer System Interface (SCSI) and Object-Based Storage Devices (OSD), are managed through the American National Standards Institute/International Committee for Information Technology Standards T10 committees. The CS1 cybersecurity group specifically addresses both network- and storage-related activities. (See the accompanying tables for examples).
Future service and applications standards supporting the implementation of cloud objectives and controls, as defined by ISO 27001 as Information Security Management, address areas of business continuity and outsourcing. Cloud computing and critical infrastructure security are another part of this CS1 group.
Principle industry associations and standards groups who focus on these evolving issues include:
The InterNational Committee for Information Technology Standards. The organization is the central U.S. forum dedicated to creating technology standards for the next generation of innovation. INCITS is accredited by the American National Standards Institute and is affiliated with the Information Technology Industry Council, a global policy advocacy organization that represents U.S. and global innovation companies.
The Distributed Management Task Force is a not-for-profit association of industry members working to simplify the manageability of network-accessible technologies through open and collaborative efforts by leading technology companies. DMTF members are dedicated to promoting enterprise and system management and interoperability.
The Storage Networking Industry Association is another prominent not-for-profit global organization, made up of member companies spanning the global storage market. SNIA’s mission is to lead the storage industry worldwide in developing and promoting standards, technologies and educational services to empower organizations in the management of information.
Working groups within SNIA’s purview include the Storage System Security group, which works to create standards for securing embedded operating systems and applications, as well as integration with IT and security infrastructure, such as external authentication services, centralized logging and firewalls. The SNIA Storage Resource Management (SRM) group is focused on securely provisioning, monitoring, tuning, reallocating and controlling storage resources so that data can be stored and retrieved. SRM also addresses storage management processes and procedures.
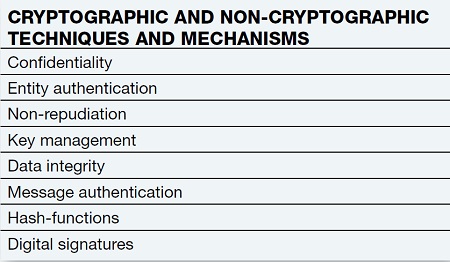
Table 2: Protection, techniques and mechanisms for security and storage, as addressed by the CS1 group of INCITSBEYOND SECURITY
Besides ensuring appropriate security for storage and private data systems, today’s media environments must also emphasize workflow performance and efficiency as the “time-to-delivery” continues to be compressed. It goes without saying that while the media and entertainment industry increases its expectations for collaboration and shared access, it still has to deal with more data and tightening of security, challenges that can no longer be simply ignored.
In today’s workspaces, storage systems must now be optimized for even greater sets of larger files. Despite increases in individual storage components (i.e., drives, tape, optical archive and even spilling over into the cloud), file systems and metadata controllers must now manage many multi-thousands to millions of files.
Recent demands are now driving file system management to the point where, in some cases, the “number of files being managed approaches billions of files,” according to Quantum/StorNext.
Beyond managing these near billions of files, enterprises now face a need for the retention of data reaching into decades. Using economical tiered storage—that is, low-cost high-capacity storage— is often mandated as the enterprise faces ever expanding retention policies of larger files with high data-rate resolutions. Organizations can, at a massive scale, extend their online storage by utilizing object storage, which reduces the bandwidth built into high-performance Tier 1 storage in exchange for more storage per cubic area of rack space.
TRANSPARENT ACCESSIBILITY
To increase productivity, simultaneous file accessibility and sharing must be achieved in both a SAN (storage area network) and a NAS (network attached storage) architecture. Regardless of the physical location, all files need to appear as though they are in the same location where they were last placed. Referred to as “transparent access,” user files should require zero intervention when asked for by either an editor, a storage tier or a media asset management system. Furthermore, this accessibility cannot change whether there are a few thousand or multi-hundreds of thousands of files.
Complex software analysis, such as that utilized in medical imaging or oil-and-gas exploration, requires high-speed storage components designed to ensure efficient workflow. Collaborative workflows, like those in medical or science applications, are routine functions for editorial media platforms. Multiple versioning with multiple elements (as in VFX or compositing) often must be shared across storage systems, which might be geographically separated by thousands of miles. This combination of requirements again opens the door for security violations; thus these workflows must also be as protected as the other topologies.
When producing thousands of versions of content for distribution (as in motion picture production), high storage throughput and consistent accessibility weigh equally against system performance and managed workflows.
These highly integrated systems also need reporting systems that can support continual analysis of performance as well as threat risks. Organizations can utilize an incident response plan to help analyze trouble, support, or if necessary, restore system functionality. For today’s complex and distributed environments, such plans may include network forensics with capabilities to track and protect data wherever it is disbursed.
When looking at how to provide a secure storage environment, questions that should be asked or solutions that should be provided include such topics as: How is your network traffic data captured today? What are the defensive measures that can help keep your data secure? Where does storage security begin for your organization?
If you’re not already looking at higher levels of system security and performance enhancements, then your facility and its assets might be at risk. You may never realize how much value there is in these assets until they are lost or compromised. It’s a new dimension in storage and system administration that heretofore wasn’t part of many organizations’ agenda, but may soon need to be.
Karl Paulsen, CPBE and SMPTE Fellow, is the CTO at Diversified Systems. Read more about this and other storage topics in his book “Moving Media Storage Technologies.” Contact Karl atkpaulsen@divsystems.com.
Get the TV Tech Newsletter
The professional video industry's #1 source for news, trends and product and tech information. Sign up below.

Karl Paulsen recently retired as a CTO and has regularly contributed to TV Tech on topics related to media, networking, workflow, cloud and systemization for the media and entertainment industry. He is a SMPTE Fellow with more than 50 years of engineering and managerial experience in commercial TV and radio broadcasting. For over 25 years he has written on featured topics in TV Tech magazine—penning the magazine’s “Storage and Media Technologies” and “Cloudspotter’s Journal” columns.
