5 Cybersecurity Tips for Broadcasting
Here’s another example of the blurring boundaries between “enterprise IT” functions and broadcast engineering: Security. Not so long ago, the IT side of the typical TV broadcaster handled Internet-facing security necessities, like email and firewalls, while the engineering side shored up distribution-related security, usually over dedicated links. Those links were plumbed in Internet Protocol (IP) but didn’t traverse the “big Internet,” so they were, in essence, cordoned off.
These days, securing the attack surfaces of broadcast and media providers is necessarily a collaboration between IT and engineering, increasingly buttressed by top-down mandates to do whatever it takes to keep the bad guys off the digital premises. Just ask TV5Monde, in France, which suffered a massive hack in April of 2015 that took down 12 of its 12 channels overnight. Like so many hacks, the bad guys had gained entry a few months earlier, maneuvering in the background to find the weak spots.
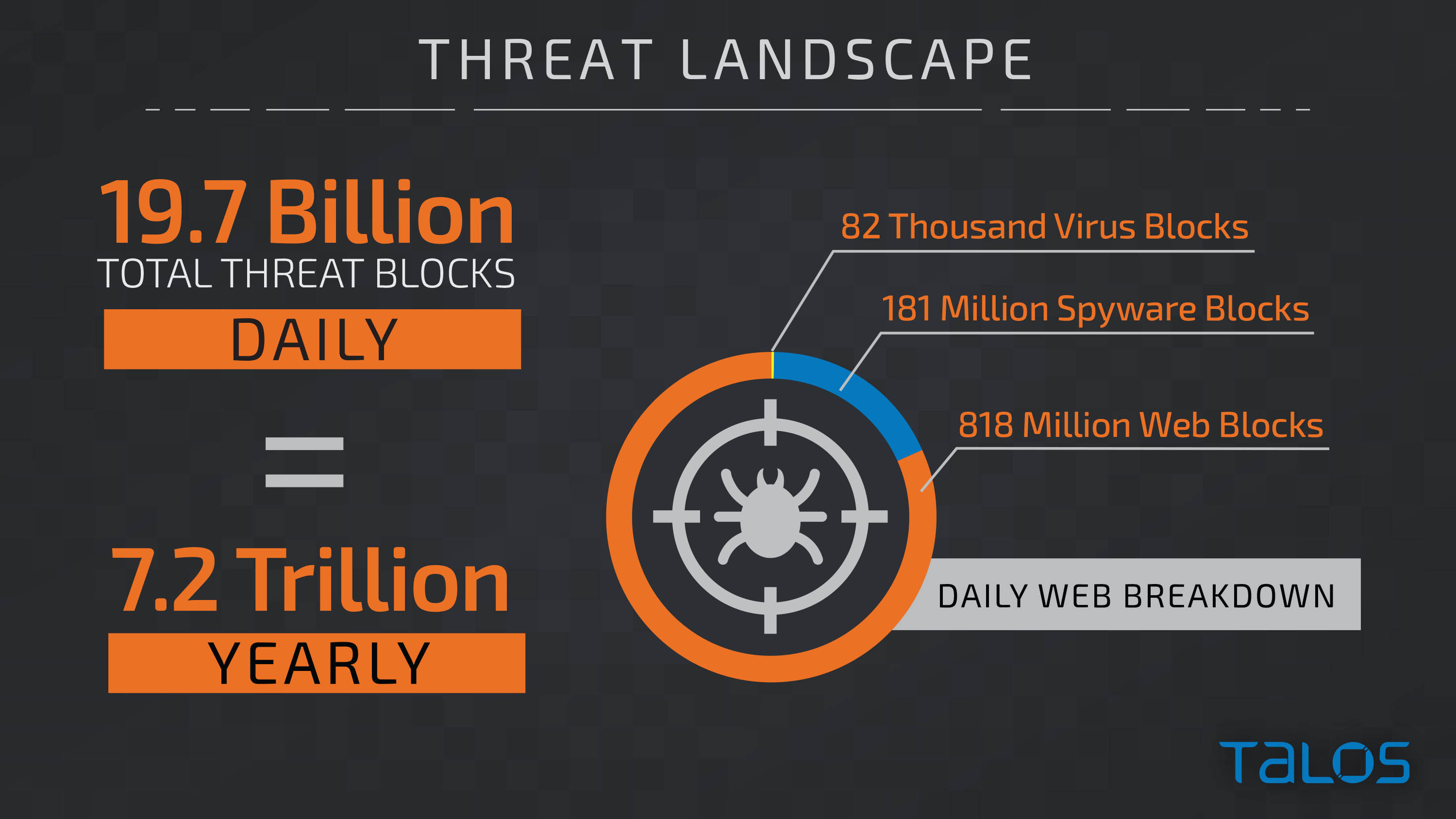
“The real-time nature of broadcast television doesn’t lend itself well to today’s time-to-detect metrics,” which can average 100 days, said Michael Korten, cyber security practice leader for Cisco. “Everyone knows the stresses that come from ads not airing, regardless of the reason.” To use a worst-case example, Super Bowl ads cost around $170,000 per second.
Korten’s group, and in particular Cisco’s Talos division –a team of nearly 300 cyber security experts– live for this stuff. They are scheduled to deliver a full readout of the latest trends during the 2018 NAB Show in Las Vegas. This will happen in the Connected Media IP Theater (which is in the South Hall, Upper Level of LVCC) on Monday, April 9, from noon to 1 p.m. They deliberately won’t compile their report until much closer to the date, so as to capture what happens between now and then. But here’s a short list of best practices and general observations they’ll likely cover:
1. You can’t protect what you can’t see –visibility is job No. 1.
The prevailing wisdom over the last two or so decades was to buy hardware to secure different types of “perimeters” –the so-called “see a problem, buy a box” solution. Each hole gets plugged with a new thumb, which is fine, until you run out of thumbs. Plus, broadcast and media companies typically average 40 to 50 individual security products. But if the firewall can’t “see” the web security product –and so on down the chain– the entirety of the threat surface can’t easily be visualized, let alone pre-emptively protected.
2. Add “time-to-detect” to your vital metrics.
According to the Talos folks, the average time-to-detect for enterprise companies (meaning beyond the media/broadcast sector) is 100 days. That’s a little over three months! How to get that vital metric down from months to hours is one of the things they’ll explain during the NAB keynote.
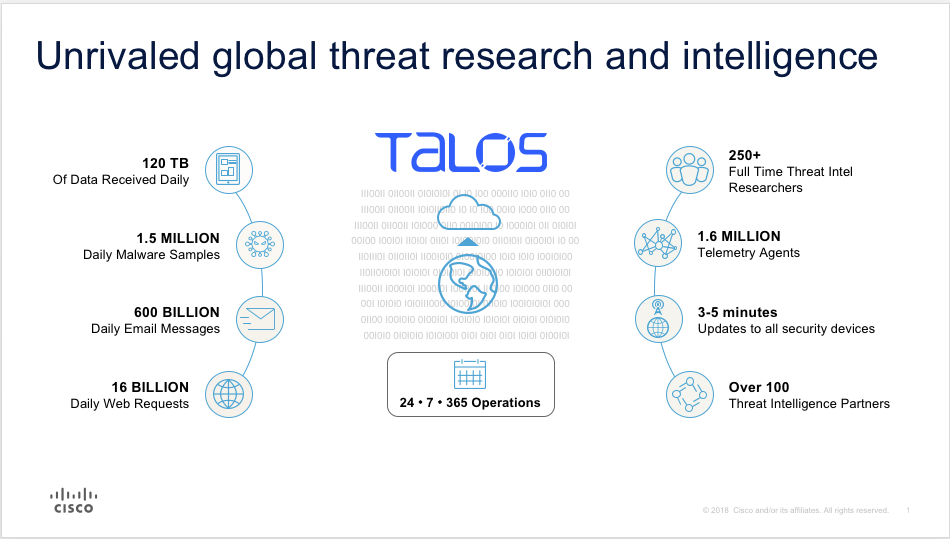
3. Know your attack entrances (which are anywhere there are end points).
E-mail is a threat surface for its potential to disseminate malicious links. Web searches can be a threat surface because of rogue DNS addresses that redirect to unsafe places. Memory sticks, remote and unsecured (non-VPN) network access, cloud handoff points, connected devices, orphaned or neglected websites –all need to be sussed out, continuously.
4. Attacks increase with each new innovation.
Whether it’s a new cloud platform, mobile offering or device, if it’s new, digital and “on-net” from production to distribution, it’s probably already being deconstructed somewhere for undesired access. Innovation cuts both ways –the intended uses and the unintended consequences. (This is why security people constantly talk about how security needs to be considered from the get-go of any new product or service and not bolted on at the end.)
5. Have a “before, during and after” plan, and check it frequently.
Improved visibility across all potential threat surfaces is step one; gaining control after a breach is step two. “The first thing people want to know, after a breach, is scope –can we contain it?” said Cisco’s Korten. “The second thing they want to know is: how bad is it? How much damage, what does remediation look like?” That’s why it’s a good idea to know what levers to pull once the alarms have sounded. (Sometimes, it’s a matter of even having levers to pull.) That means a security blueprint with perimeter detection and a “cloud firewall” designed for real-time threat management and automation. Overall mission: Stay ahead of the hack.
The grim reality about broadcast TV and security is this: Attackers have unlimited opportunities to get where they want to go. They’ll keep trying and trying and trying. We’re likely see more evidence of this, even in the short run-up to the 2018 NAB Show. If this is a topic near and dear to your day-to-day, it might make sense to check out the Talos presentation and the rest of its security portfolio while you’re in Vegas.
This is the third in a six-part blog series preceding the 2018 NAB Show. Click here to read more about what broadcasters will be talking about at this year's show.
About the Author: Leslie Ellis is a respected “technology translator,” known in cable and telecom circles for her award-winning, 20+ year “Translation Please” column in Multichannel News. She took on this Cisco-sponsored pre-NAB series to point out common and frustrating obstacles, for anyone on the sliding transition toward “being more Internet-like.” It is less of a comprehensive representation of available options and more a glimpse into what’s worrisome, on a day-to-day basis for engineers and IT people who work in media and entertainment.
Get the TV Tech Newsletter
The professional video industry's #1 source for news, trends and product and tech information. Sign up below.
